Switches have a finite table in which they store mappings of MAC addresses with ports. When this table overflows, the switch usually does one of the two things:
1. Operates as a hub, repeating all incoming frames to all other ports, this effectively combining all ports on the switch into one collision domain.
2. Locks up entirely, discarding all incoming frames.
On a network with a switch which fails operating effectively as a hub when the MAC address table is filled, an attacker can flood the switch with frames containing bogus MAC addresses. This overflows its state table and forces it to operate as a hub.
However, there are limitations to this approach. Many switches do not fail as hubs when their table fills. Because of these limitations, other attack methods are used instead, such as ARP cache poisoning.
ARP Cache Poisoning
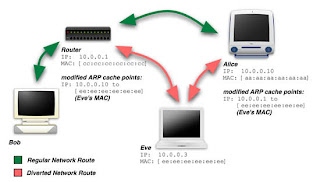
1. Attacking host Eve sends spoofed ARP packets to the victim host Alice. This poisons the ARP table on host Alice so that it associates the Eve's MAC address (ee:ee:ee:ee:ee:ee) with the IP address of Router 10.0.0.1.
2. Attacking host Eve send spoofed ARP packets to the router. This poisons the ARP table on the router R so that it associated the MAC address of the attacking host Eve with the IP address of the victim Alice 10.0.0.10.
3. Attacking host Eve routes all traffic between Alice and the router which sniffing the traffic flowing through Eve.
Perform ARP Cache Poisoning with ARP Replies
Using arp command to manually poison ARP table
One of the methods of poisoning ARP tables uses ARP responses to exploit a vulnerability in most ARP cache, that system will accept any ARP response updating that entry, even if that system never sent out an ARP request.
This ARP reply cache poisoning method can be performed manually using the arp command.
#arp -s other-host other-MAC-address pub
The -s option is legitimately useful for implementing ARP proxies, but can also be used by attackers to carry out cache poisoning.
In addition to manually poison ARP tables, automated tools are also available with streamline ARP cache poisoning. The dsniff suite of software includes the arpspoof utility which cleanly poisons ARP caches on the victim, then cleans up the victim's ARP cache upon exit. It also can be used to attack all the hosts in the broadcast domain.
Information about arpspoof and dsniff can be found at http://www.monkey.org/~dugsong/dsniff/
A good example of executing arpspoof can be found at http://www.irongeek.com/i.php?page=security/arpspoof&mode=print
Poisoning ARP table is the first step to compromise the target host. Once attackers successfully poison the ARP tables, they can start the real attacks against your host like poisoning DNS caches and redirecting target host's browser to forged web pages.

